U-Boot for Zynq is capable to authenticate and decrypt bitstream/images from the command line. Both zynqrsazynq rsa/zynqaes zynq aes commands works getting the image from the DDR memory, allowing the images be loaded from wide variety of sources (flash memory, TFTP sever...).
The images have to be generated using bootgen with proper authentication and encryption keys.
Table of Contents
U-Boot configuration
By default this feature is disabled in the default U-Boot/Petalinux configurations, so both CONFIG_CMD_ZYNQ_RSA and CONFIG_CMD_ZYNQ_AES needs to be enabled in the U-Boot configuration file.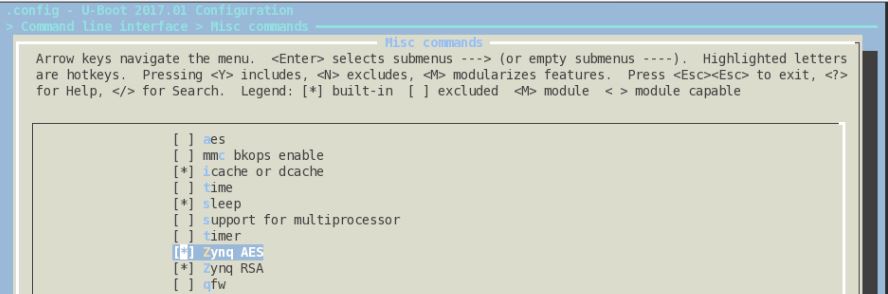
| Code Block |
|---|
|
zynqaeszynq aes - Zynq AES decryption
Usage:
zynqaeszynq zynqaesaes [operation type] <srcaddr> <srclen> <dstaddr> <dstlen> -
Decrypts the encrypted image present in source address
and places the decrypted image at destination address
zynq zynqaesaes operations:
zynqaeszynq aes <srcaddr> <srclen> <dstaddr> <dstlen>
zynqaeszynq aes load <srcaddr> <srclen>
zynqaeszynq aes loadp <srcaddr> <srclen>
if operation type is load or loadp, it loads the encrypted
full or partial bitstream on to PL respectively. If no valid
operation type specified then it loads decrypted image back
to memory and it doesnt support loading PL bistsream |
| Code Block |
|---|
|
Zynq> zynq rsa
zynqrsazynq zynqrsarsa - Zynq RSA verfication
Usage:
zynqrsazynq zynqrsarsa <baseaddr> - Verifies the authenticated and encrypted zynq images |
Loading authenticated/encrypted bitstream
Encrypted bitstream
Create a BIF file to be used for the encrypted bitstream generation process and use bootgen to generate it.
| Code Block |
|---|
|
all:
{
[aeskeyfile] key.nky
[encryption = aes] download.bit
}
|
| Code Block |
|---|
|
bootgen -image bitstream.bif -arch zynq -process_bitstream bin -encrypt efuse |
Boot up to U-Boot and use the zynqaes command to load the encrypted bitstream
| Code Block |
|---|
|
Zynq> fatload mmc 0 1000000 download.bit.bin
reading download.bit.bin
4044652 bytes read in 234 ms (16.5 MiB/s)
Zynq> zynqaeszynq aes load 1000000 ${filesize}
zynq_decrypt_load: FPGA config done |
Note: this feature does not work with eFUSE stored keys for U-Boot released bellow 2018.1Authenticated bitstream
Content under developmentLoading authenticated/encrypted images
Encrypted images
Create a BIF file to be used for the encrypted image generation process and use bootgen to generate it. Split option is required for bootgen in order to get encrypted image without boot header, this way the dummy partition will include the boot header and the image will be splited in a encrypted way.
| Code Block |
|---|
|
all:
{
[aeskeyfile] key.nky
[bootloader, encryption=aes] zynq_fsbl.elf
[encryption = aes] image.ub
} |
| Code Block |
|---|
|
bootgen -w -image images.bif -arch zynq -o images.bin -encrypt efuse -split bin |
Boot up to U-Boot and use the
zynqaes zynq aes command to decrypt the encrypted image.
| Code Block |
|---|
|
Zynq> fatload mmc 0 0x1000000 image.ub.bin
reading image.ub.bin
10147564 bytes read in 565 ms (17.1 MiB/s)
Zynq> zynq zynqaesaes 0x1000000 0x9ad6ec 0x2000000 0x9ad3d0 |
Note: This feature does not work for U-Boot released bellow 2018.1Authenticated images
Create a BIF file to be used for authenticated image generation process and use bootgen to generate it. The partitions authenticated by U-Boot can be specified by the attribute partition_owner, and load attribute to set the address where authenticated partition will be loaded. The current implementation requires at least two partition be present before the first U-Boot owned partition.
| Code Block |
|---|
|
all:
{
[pskfile] psk.pem
[sskfile] ssk.pem
[bootloader, authentication=rsa] zynq_fsbl.elf
[authentication=rsa] u-boot.elf
[authentication=rsa, load = 0x3000000, partition_owner=uboot] image.ub
} |
| Code Block |
|---|
|
bootgen -w -image images.bif -arch zynq -o images.bin |
Boot up to U-Boot and use the
zynqrsa zynq rsa command to authenticate the boot image.
| Code Block |
|---|
|
Zynq> fatload mmc 0 0x1000000 images.bin
reading images.bin
15157504 bytes read in 1263 ms (11.4MiB/s)
Zynq> zynq zynqrsarsa 0x1000000
UBOOT is not Owner for partition 0
UBOOT is not Owner for partition 1
Zynq> bootm 0x3000000 |
Encrypted and Authenticated images
Create a BIF file to be used for image generation process and use bootgen to generate it.
| Code Block |
|---|
|
all:
{
[aeskeyfile] key.nky
[pskfile] psk.pem
[sskfile] ssk.pem
[bootloader, encryption=aes, authentication=rsa] zynq_fsbl.elf
[encryption=aes, authentication=rsa] u-boot.elf
[encryption=aes, authentication=rsa, load = 0x3000000, partition_owner=uboot] image.ub
} |
| Code Block |
|---|
|
bootgen -w -image images.bif -arch zynq -o images.bin -encrypt efuse |
Boot up to U-Boot and use the
zynqrsa zynq rsa command to authenticate and decrypt the boot image.
| Code Block |
|---|
|
Zynq> fatload mmc 0 0x1000000 images.bin
reading images.bin
15157504 bytes read in 1263 ms (11.4MiB/s)
Zynq> zynq zynqrsarsa 0x1000000
UBOOT is not Owner for partition 0
UBOOT is not Owner for partition 1
Zynq> bootm 0x3000000 |
- Title 1 & Link 1
- Title 1 & Link 1